
We’re excited to hear your project.
Let’s collaborate!

With popularity comes trouble... In this case here meaning: security vulnerabilities and risky over-exposure to cyber threats. And this can only mean that securing your website, that's running on the currently third most popular CMS in the world, calls for a set of Drupal security best practices for you to adopt.
And to stick to!
There's no other way around it: a set of strategically chosen security measures, backed by a prevention-focused mindset, pave the shortest path to top security.
Stay assured: I've selected not just THE most effective best practices for you to consider adopting, but the easiest to implement ones, as well.
Quick note: before I go on and knee-deep into this Drupal security checklist, I feel like highlighting that:
And now, here are the tips, techniques, and resources for you to tap into and harden your Drupal site's security shield with.
Consider enforcing some security measures at your Drupal database level, as well.
It won't take you more than a few minutes and the security dangers that you'll be safeguarding it from are massive.
Here are some basic, yet effective measures you could implement:
Note: for changing your table prefix you can either navigate to phpMyAdmin, if you already have your Drupal site installed, or do it right on the setup screen (if it's just now that you're installing your website).
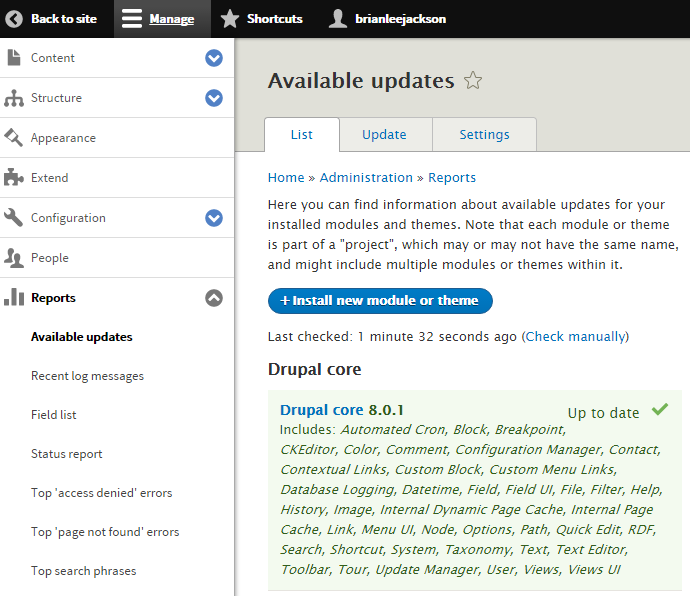
And this is the least you could do, with a significant negative impact on your Drupal site if you undermine its importance. If you neglect your updating routine.
Do keep in mind that:
Why should you leave it recklessly exposed? Running on an outdated Drupal version, packed with untrusted Drupal modules and themes?
Especially since keeping it up to date means nothing more than integrating 2 basic Drupal security best practices into your site securing “routine”:
And here's another one of those underrated and too often neglected Drupal security best practices!
Why should you wait for a ransomware attack and realize its true importance... “the hard way”?
Instead, make a habit of regularly backing up your website since, as already mentioned:
There's no such thing as perfection when it comes to securing a Drupal site, there's only a hierarchy of different “security levels” that you can activate on your site
And backing up your site, constantly, sure stands for one of the most effective measures you could apply for hardening your Drupal website.
Now, here's how you do it:
There, now you can stay assured that, if/when trouble strikes, you always have your backup(s) to retrieve your data from and get back “on your feet” in no time!
No need to get all “altruist” when it comes to your bandwidth!
And to share it with all kinds of scrappers, bad bots, crawlers.
Instead, consider blocking their access to your bandwidth right from your server.
Here's how:
Add the following code to your .htacces file and block multiple user-agent files at once:
RewriteEngine On
RewriteCond %{HTTP_USER_AGENT} ^.*(agent1|Wget|Catall Spider).*$ [NC]
RewriteRule .* - [F,L]
Or use the BrowserMatchNoCase directive as follows:
BrowserMatchNoCase “agent1” bots
BrowserMatchNoCase "Wget" bots
BrowserMatchNoCase "Catall Spider" bots
Order Allow,Deny
Allow from ALL
Deny from env=bots
Use the KeyCDN feature for preventing those malicious bots from stealing your bandwidth!
More often than not “easy” doesn't mean “less efficient”.
And in this particular case here, simply opting for a strong username (smarter than the standard “admin”) and password can make the difference between a vulnerable and a hard-to-hack Drupal site.
For this, just:
Manually change your credentials right from your admin dashboard: “People” → “Edit”→ “Username” while relying on a strong password-generating program ( KeePassX or KeePass)
Would you knowingly risk your users' sensitive data? Their card information let's say, if it's an e-commerce Drupal site that you own?
And how about your login credentials?
For this is what you'd be doing if — though you do recognize the importance of using an SSL certificate — you'd still put this measure at the back of your list of Drupal security best practices.
In other words, running your site on HTTPs (preferably on HTTP/2, considering all the performance benefits that it comes packaged with) you'll be:
For they sure make your most reliable allies when it comes to tracking down loopholes in your site's code or preventing brutal cyber attacks.
From:
… and so on, these Drupal modules will be “in charge” of every single aspect of your site's security strategy.
And supercharging your site with some of the most powerful Drupal security modules is, again, the easiest, yet most effective measure you could possibly enforce.
Now speaking of these powerful modules, here's a short selection of the “must-have” ones:
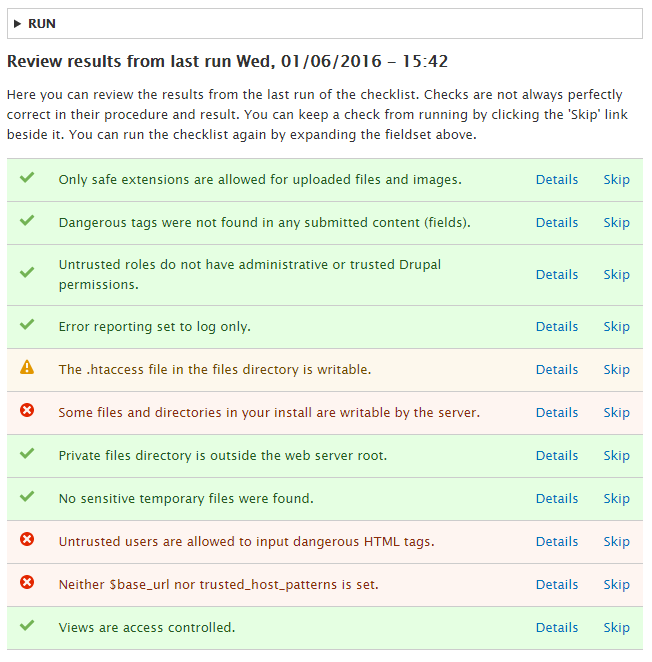
Another one of those too-easy-to-implement, yet highly effective Drupal security best practices to add to your Drupal security checklist:
Implementing (and updating) HTTP security headers
“Why bother?”
Cause:
Ensure that your file permissions for:
… aren't too dangerously loose.
Since such negligence could easily turn into an invitation for “evil-minded” intruders!
And it's on Drupal.org's dedicated page that you can find more valuable info on this apparently insignificant, yet extremely effective security measure
Told you this was going to be a list of exclusively easy-to-implement Drupal security best practices.
Blocking access to sensitive files on your website (the upgrade.php file, the install.php file, the authorize.php file etc.) won't take you more than a few minutes.
But the danger you'd avoid — having a malicious intruder risking to access core files on your Drupal site — is way too significant to overlook.
END of the list! These are probably the easiest steps to take for securing your Drupal site.
How does your own list of Drupal security tips, techniques, and resources to tap into look like?

We’re excited to hear your project.
Let’s collaborate!